


Global entities confront intensifying cybersecurity threats fueled by emerging tech adoption, geopolitical instability, and sprawling supply chain risks, demanding urgent collaborative action.
ALTEN "Tech Week" webinar delved into Cybersecurity & AI Management, attracting cross-industry professionals. Expert Miriam unpacked AI’s dual roles: covering real-world cases including anomaly detection, big data analytics, advanced social engineering attacks, and AI-generated malware.
Key Characteristics:
Code mutation: Automatically restructures its code when infecting new devices to avoid signature matching
Encryption obfuscation: Hides malicious behavior using encryption to bypass static analysis
Zero-day exploitation: Frequently leverages undisclosed vulnerabilities
Cutting-Edge Countermeasures
Current industry best practices against these evolving threats include:
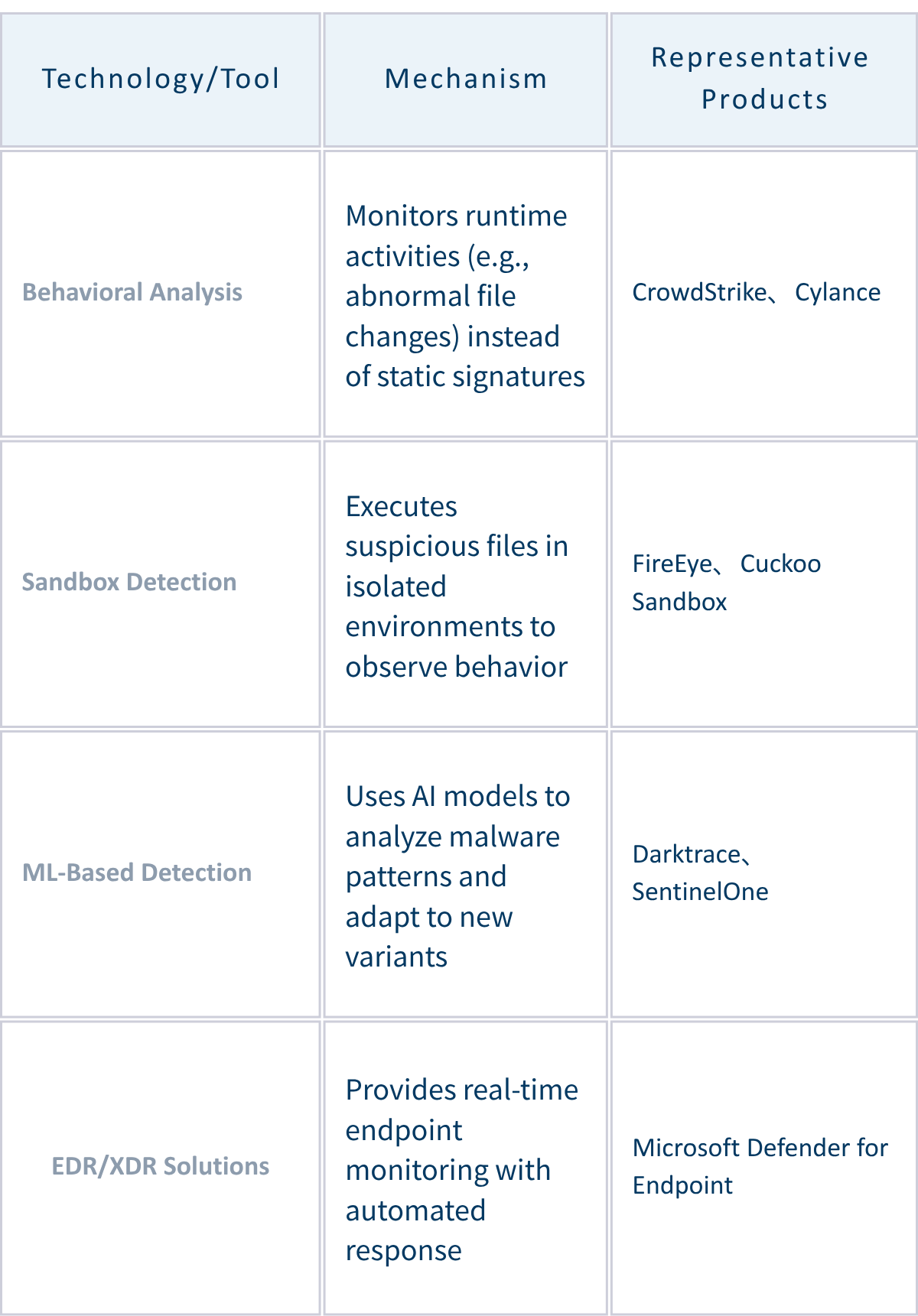
Key Recommendation: Enterprises should adopt layered defense strategies combining behavioral analysis, AI detection, and real-time response mechanisms rather than relying on single solutions.
AI"s Dual Role in Cybersecurity
Miriam highlighted AI"s growing importance in combating advanced threats through:
Anomaly Detection:Identifies deviations from established behavioral baselines
Automated Remediation:Isolates compromised devices without human intervention
Threat Intelligence:Analyzes global attack data to predict emerging tactics
Challenge: AI models remain vulnerable to adversarial attacks, requiring continuous training data updates.
Enterprise Security Best Practices
Red Teaming:Simulate polymorphic malware attacks to test defenses
Zero Trust:Enforces continuous verification of all access requests
Employee Training: Critical since polymorphic malware often spreads via phishing
Closing Insights
The host concluded by emphasizing cybersecurity as an ongoing evolution. Participants were encouraged to:
Request tailored security assessments from ALTEN"s technical team
Explore MITRE ATT&CK"s framework for polymorphic malware tactics (e.g., T1574 - Hijack Execution Flow)
Join future "Tech Week" sessions covering cloud security and data privacy
"In security, the goal isn’t to eliminate risks entirely, but to manage them effectively."
Recommended Resources: